Build a Live HTTP Request Sniffer in GitHub Codespaces with Flask
✅ Why This Project?
- Verify URL fetches: Paste your public URL into any client (Copilot, webhook sender, etc.) and see if it hits your endpoint.
- Inspect details: Capture method, path, query, headers, IP, and body preview.
- Zero setup: Runs entirely in Codespaces—no local environment headaches.
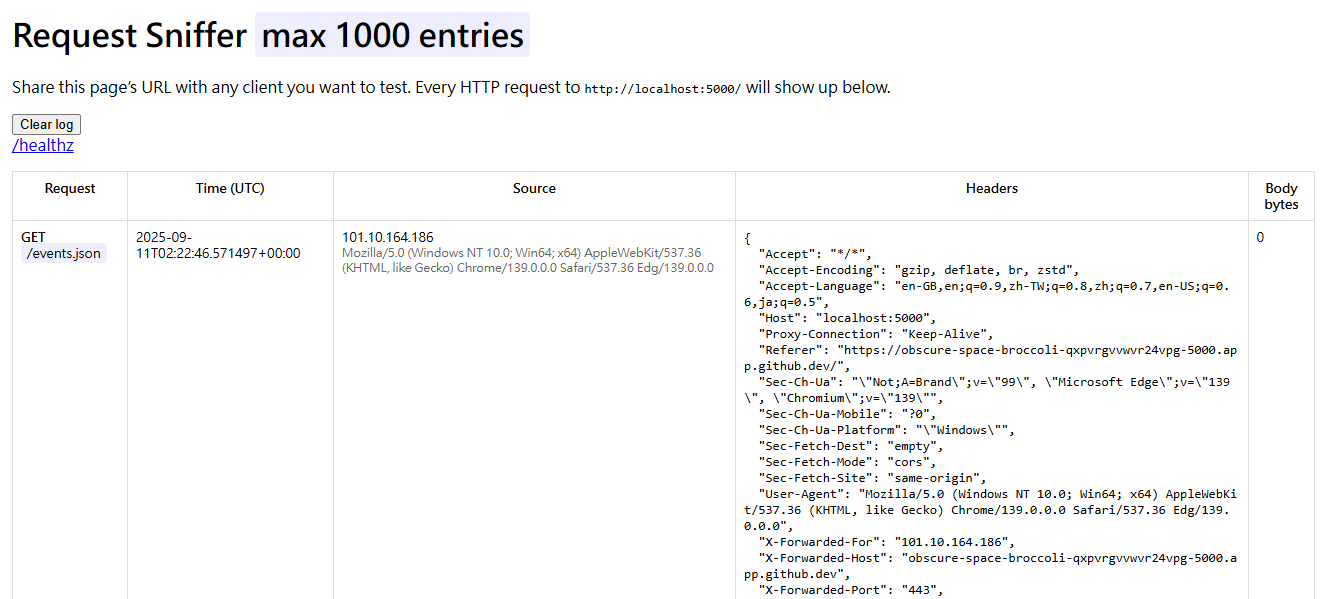
🔍 What It Does
- Logs every HTTP request (GET, POST, PUT, PATCH, DELETE, OPTIONS).
- Displays:
- Timestamp (UTC)
- Client IP (with
X-Forwarded-Forsupport) - User-Agent
- Headers
- Body size and preview (pretty-printed JSON if applicable)
- Live-updating dashboard at
/. - JSON feed at
/events.json. - Catch-all route for arbitrary paths (so POSTs to
/hookor/testsucceed). - Utility endpoints:
/healthzand/clear.
🚀 Quickstart in GitHub Codespaces
Create a new repo and add:
requirements.txt:1flask==3.0.3app.py(see full code in the repo).
Open in Codespaces:
- On GitHub: Code → Create codespace on main.
Install & run:
1 2 3 4python3 -m venv .venv source .venv/bin/activate pip install -r requirements.txt python app.pyExpose the app:
- In the PORTS panel, set port
5000to Public. - Copy the public URL (e.g.,
https://5000-<id>.app.github.dev/).
- In the PORTS panel, set port
🧪 Test It
Open the dashboard at /—you’ll see your own GET request logged.
Try some POSTs:
| |
Watch them appear in real time.
🔒 Security Notes
- Public means anyone with the URL can send requests.
- Logs are in-memory only; restart clears them.
- Don’t share sensitive data.
🕵️ Use Case: Does Copilot Fetch URLs?
Paste your Codespaces URL into the assistant you’re testing. If it fetches, you’ll see:
- User-Agent (often reveals the service)
- IP (usually a proxy or cloud region)
- Timestamp
If nothing shows up, that client likely doesn’t make external requests.
🌟 Why Codespaces?
- No local setup.
- Public URL in seconds.
- Perfect for quick experiments and demos.
👉 View the Repo on GitHub
https://github.com/chienhsiang-hung/copilot-request-detector