AWS Deploy Lambda Function, API Gateway, Invoke/Call another Lambda Function, Save to S3, Public Access etc.
Flow Outline
Structure
(ABSTRACT EXAMPLE)
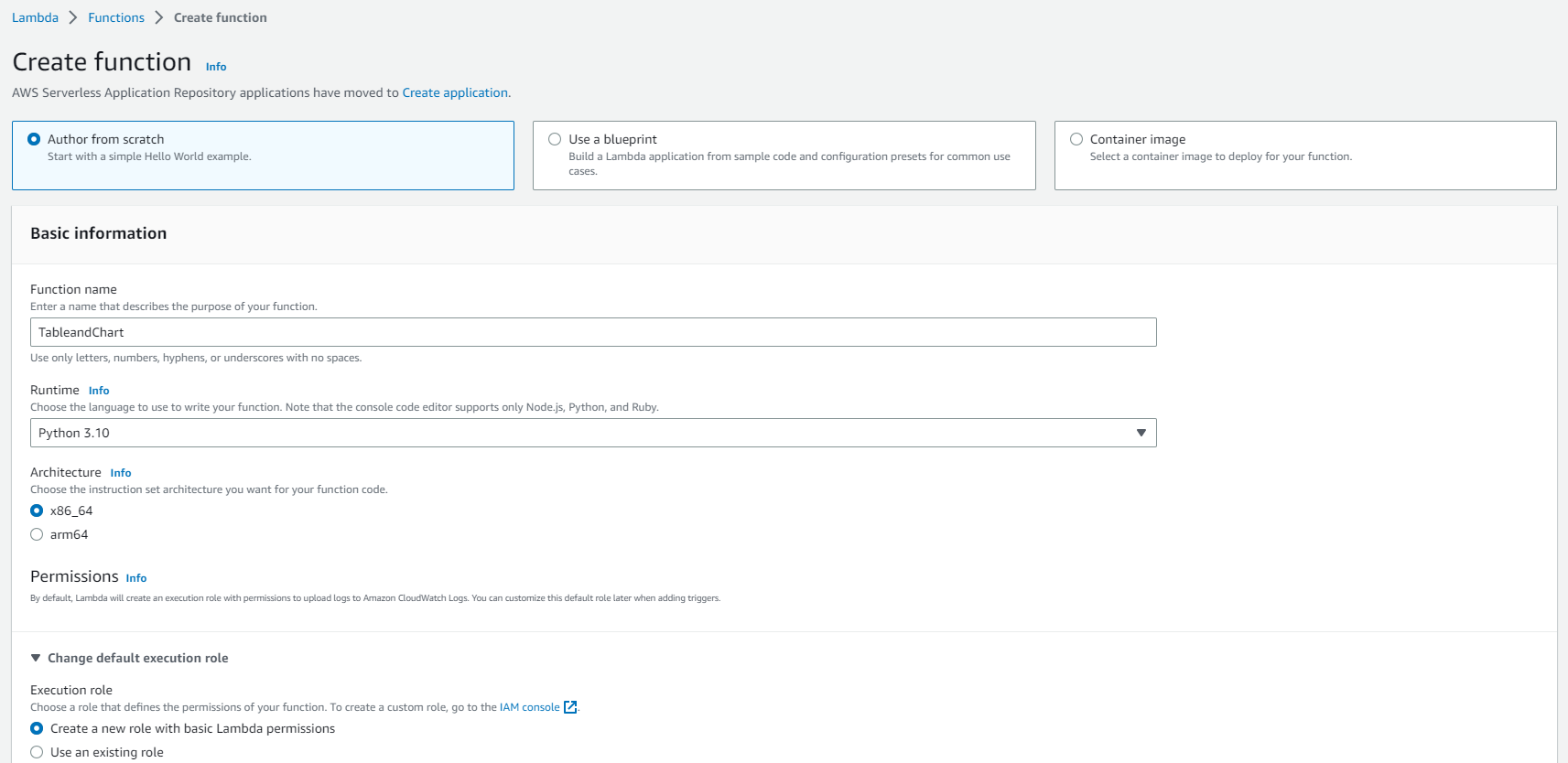
TableandChart
- Code
- Python 3.9 (Architecture x86_64), HTML and CSS
- main package - matplotlib
- Python 3.9 (Architecture x86_64), HTML and CSS
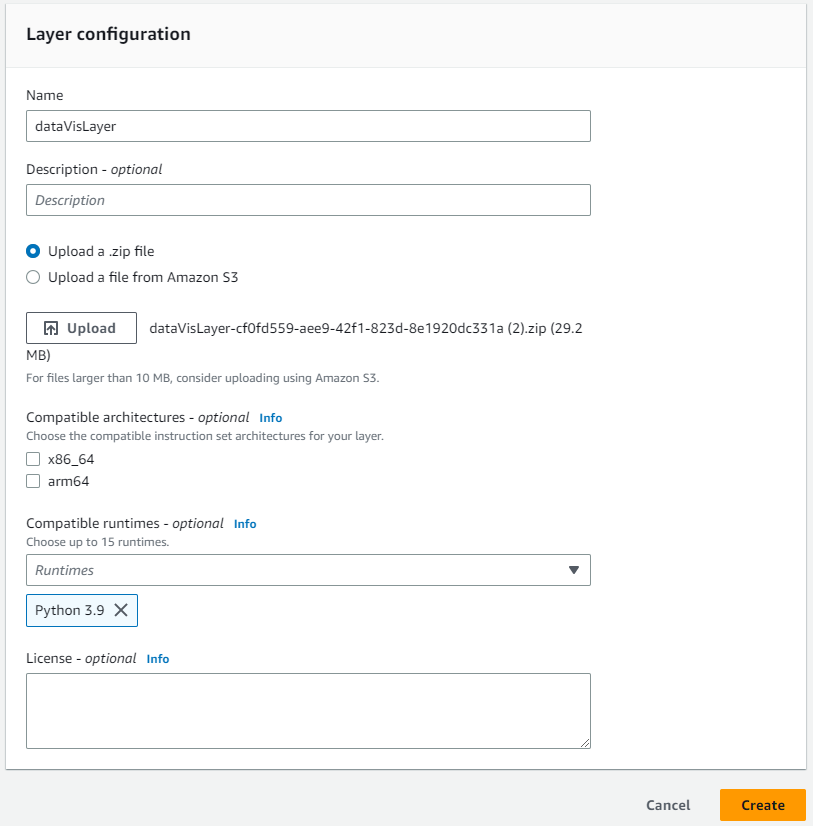
- Layers
- dataVisLayer (custom)
- AWSDataWrangler-Python39
- numerize (custom)
HtmltoPDF
- Code
- Python 3.9 (Architecture x86_64)
- main package - pandas, PyPDF2
- custom-fonts
- Python 3.9 (Architecture x86_64)
- Layers
- wkhtmltopdf
- pandas
- fonts
- PyPDF2
How to Deploy a Lambda Function
Regions
First check your region.

Create function
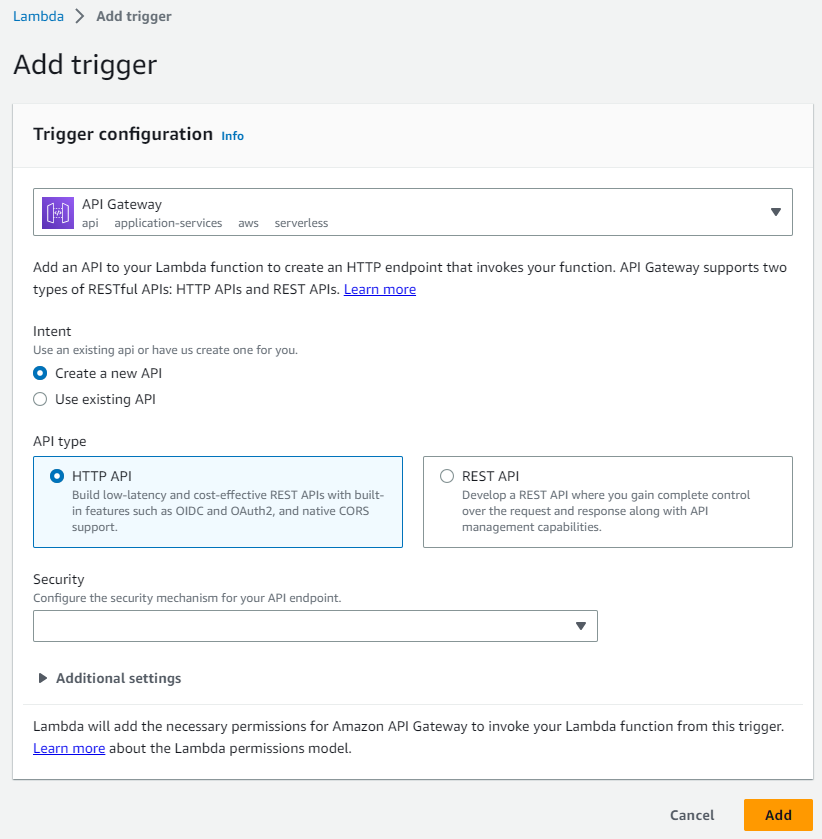
Add trigger (API Gateway)

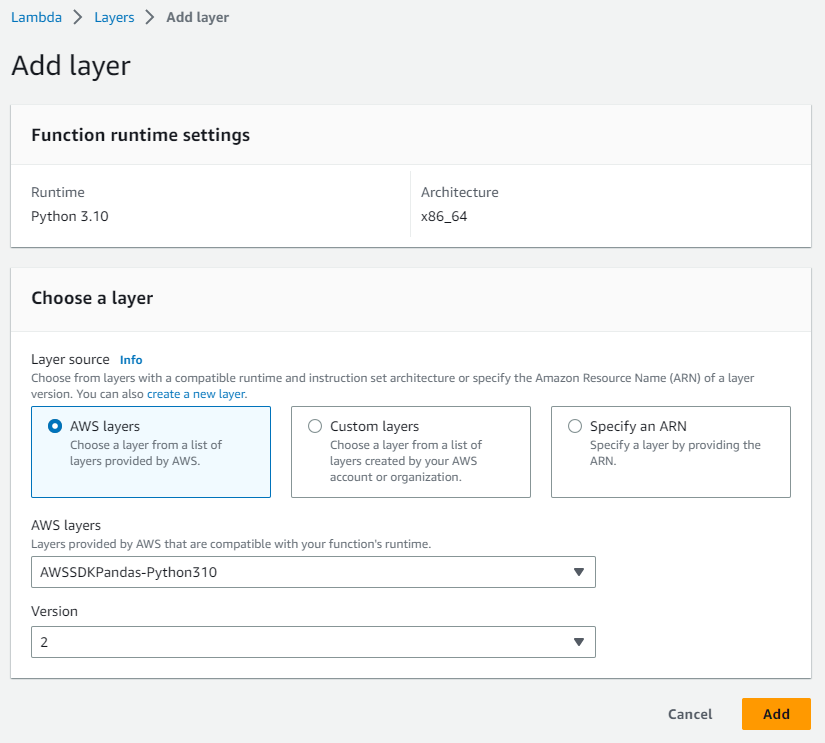
Layers
2 ways to add layers
- Add layer
AWSSDKPandas-Python310at the Functions page (AWSDataWrangler-Python39upgrades toAWSSDKPandas-Python310)
Add-AWS-layers-AWSSDKPandas-Python310.png
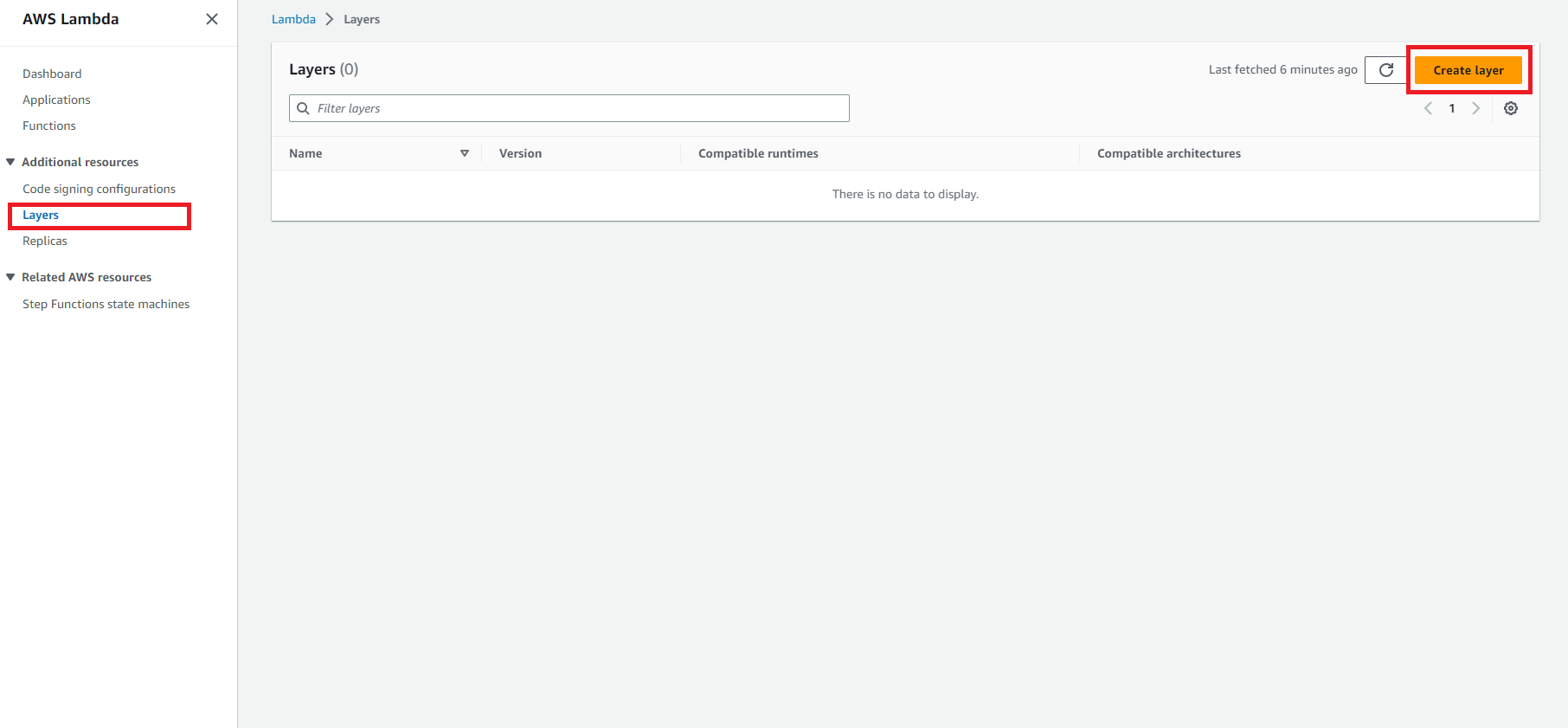
If you can’t find the ARN or you need to customize some packages inside.
Including library dependencies in a layer:
Layer paths for each Lambda runtime | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Runtime | Path | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Node.js |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Python |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Java |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Ruby |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
All runtimes |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
See Creating and sharing Lambda layers - AWS Lambda (amazon.com).
Runtime Check
Remember to check your function runtime. Make sure the runtime of layers and the function are the same.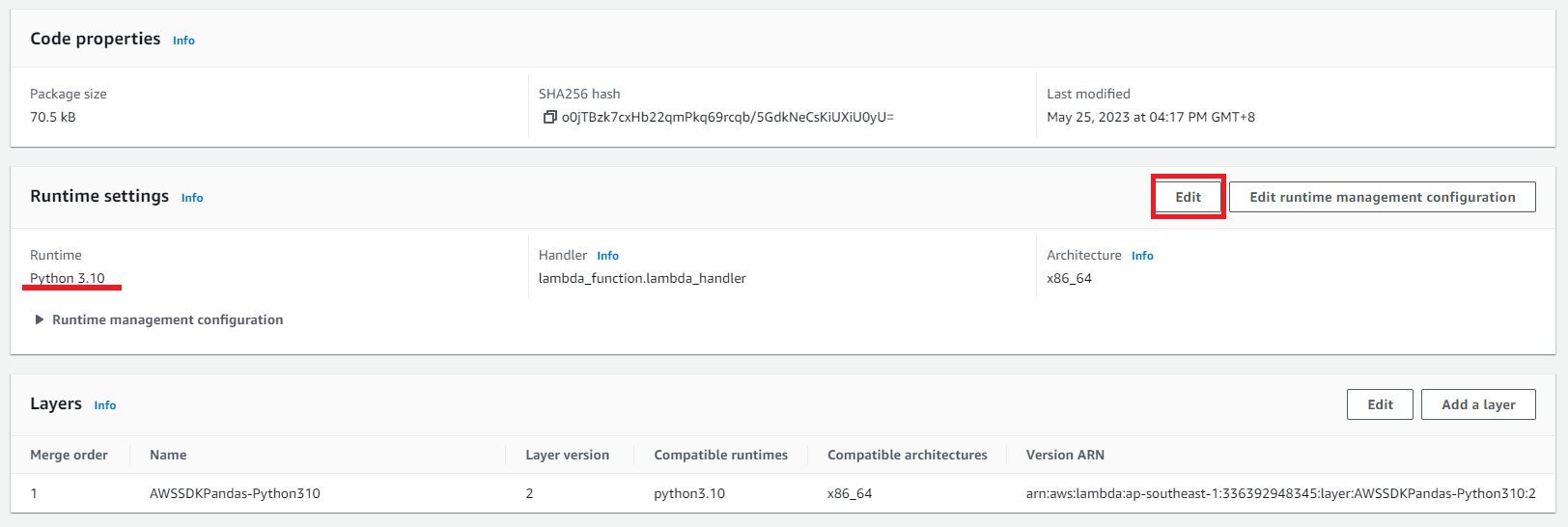
AWS Data Wrangler
And, for AWSDataWrangler-Python39 (PythonXX should meet your runtime version as well), the ARN should be arn:aws:lambda:YOUR-REGION:336392948345:layer:AWSDataWrangler-Python39:2. For example, AWS Data Wrangler Lambda Layer - 2.15.0 (Python 3.9) and region Singapore will be arn:aws:lambda:ap-southeast-1:336392948345:layer:AWSDataWrangler-Python39:2.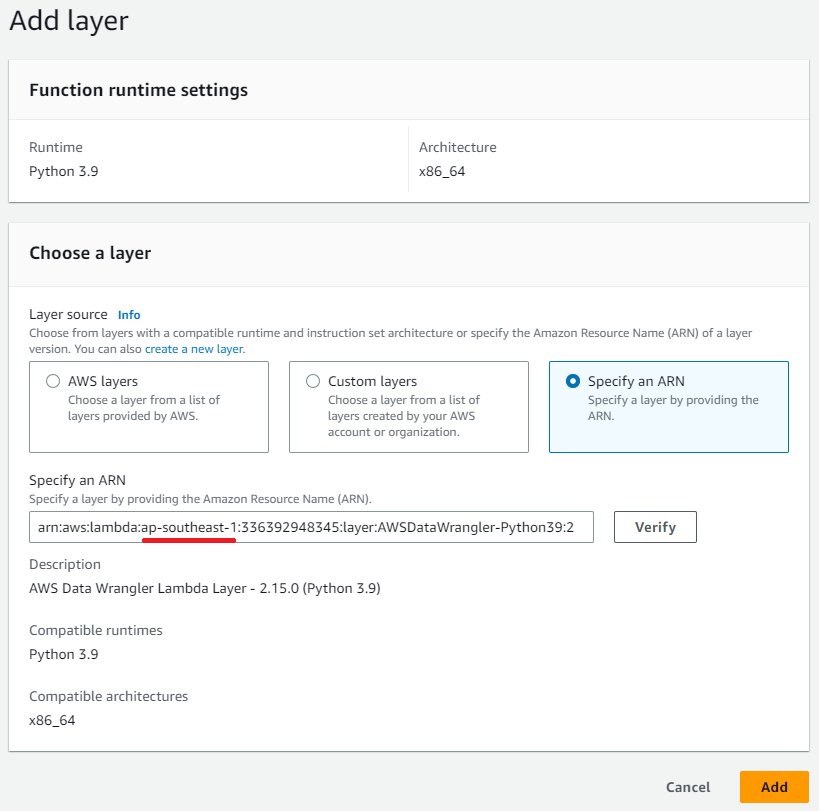
Configuration
Timeout
Task timed out after 3.09 seconds…
General configuration Timeout 3 sec (default) set to 10 min (max).
Existing role
And, from here, choose an Existing role.
Environment variables
(For HtmltoPDF function)
Roles
Create role
to create a role and add permission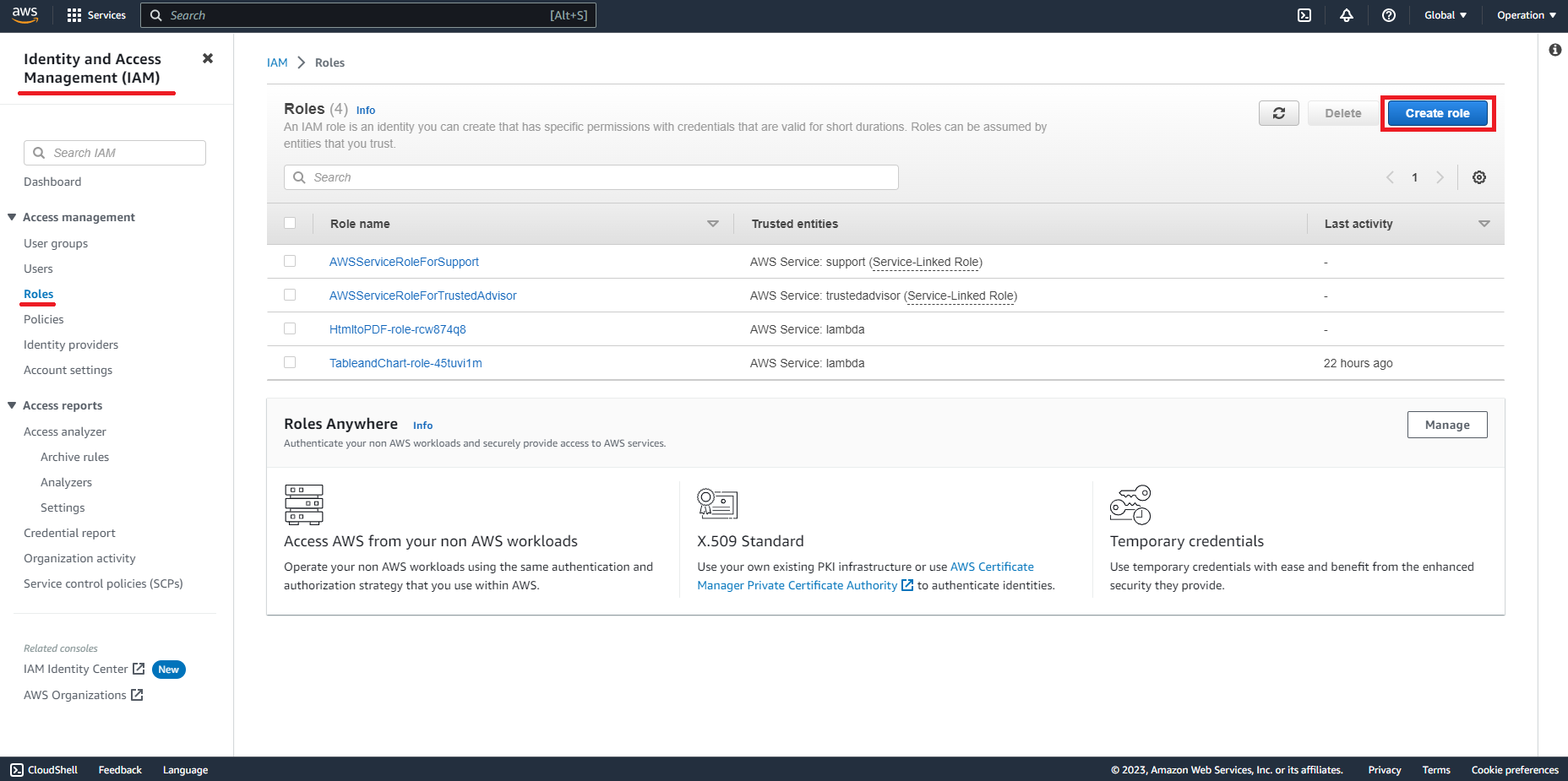

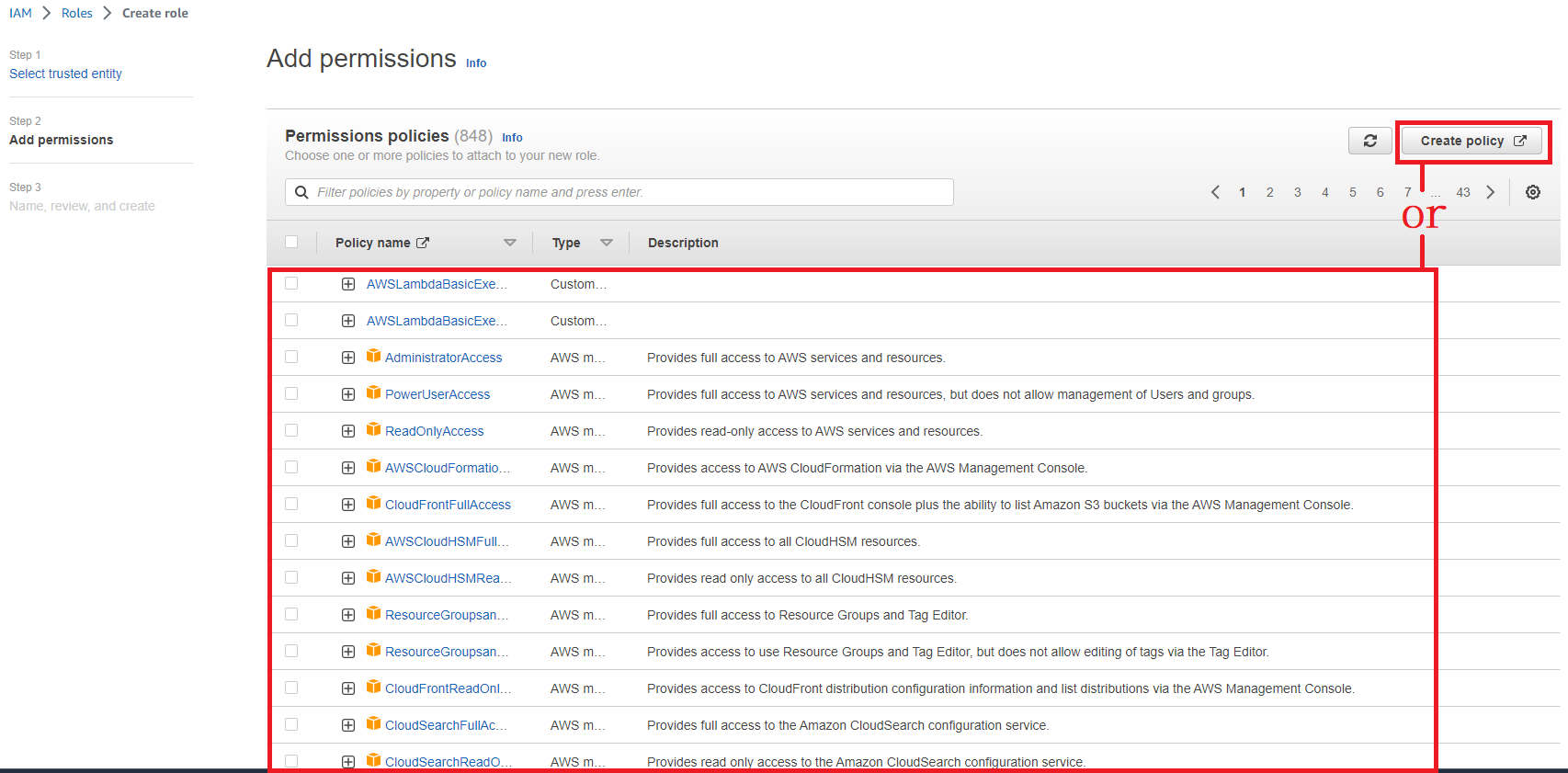
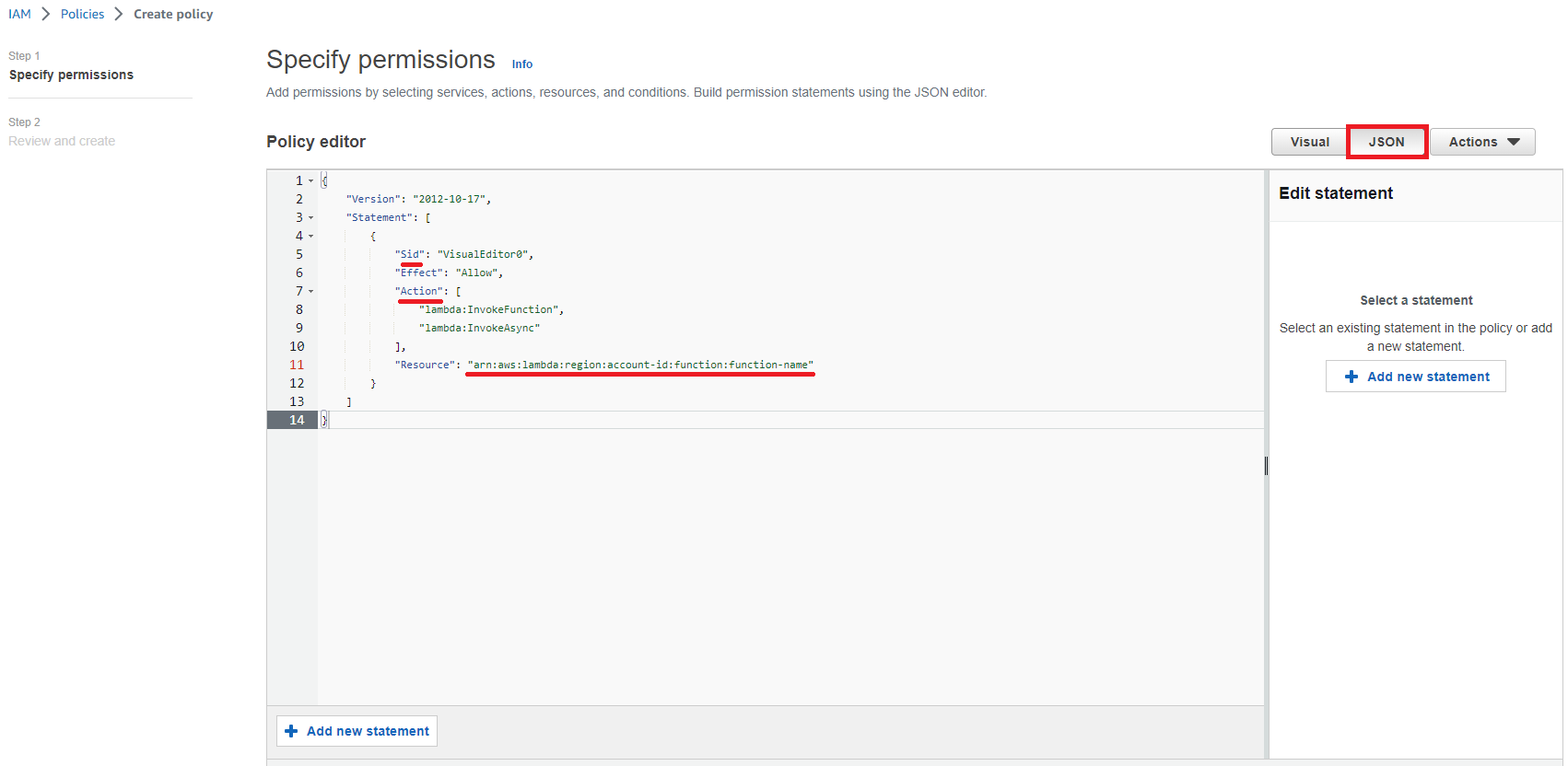
Invoke Role
To invoke another lambda function in AWS.
Permissions policies - Customer managed -
InvokeHtmltoPDF1 2 3 4 5 6 7 8 9 10 11 12 13 14{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "lambda:InvokeFunction", "lambda:InvokeAsync" ], "Resource": "arn:aws:lambda:region:account-id:function:function-name" } ] }Resource: lambda function arn1, replaceregion,account-idandfunction-name.Permissions policies - AWS managed -
AWSLambdaBasicExecutionRole1 2 3 4 5 6 7 8 9 10 11 12 13 14{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents" ], "Resource": "*" } ] }
lambda to s3
lambda-s3-role
- Permissions policies - AWS managed -
AWSLambdaExecute1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "logs:*" ], "Resource": "arn:aws:logs:*:*:*" }, { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:PutObject" ], "Resource": "arn:aws:s3:::*" } ] }
Amazon S3
Create bucket
Configuration
General configuration
Bucket name (Bucket with the same name already exists: Bucket name must be globally unique and must not contain spaces or uppercase letters. See rules for bucket naming)
wampdfswam-consolidated-pdfsAWS Region
Singapore
Object Ownership
- ACLs enabled
- Bucket owner preferred
Block Public Access settings for this bucket
- untick
Block all public access - I acknowledge that the current settings might result in this bucket and the objects within becoming public.
Bucket Versioning - Disable
Default encryption
Encryption key type
Amazon S3 managed keys (SSE-S3)Bucket Key
Disable
Advanced settings
Object Lock
Disable
Object URL
For it to work publicly, you need to add a Bucket policy to make the Bucket Publicly accessible.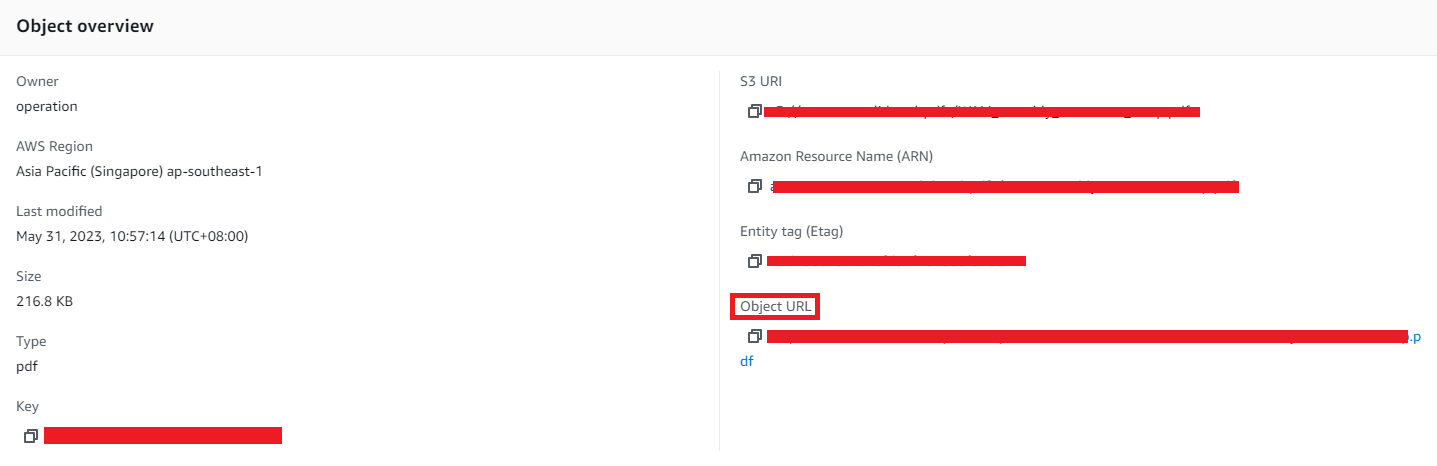
| |
Replace the Resource with your Bucket.
Be careful, the objects in this bucket will all be publicly available by default. So don’t leak your Object URL (bucket name and file name) out.
Once you’ve applied the policy successfully, you will see the changes made in the Permission overview sector.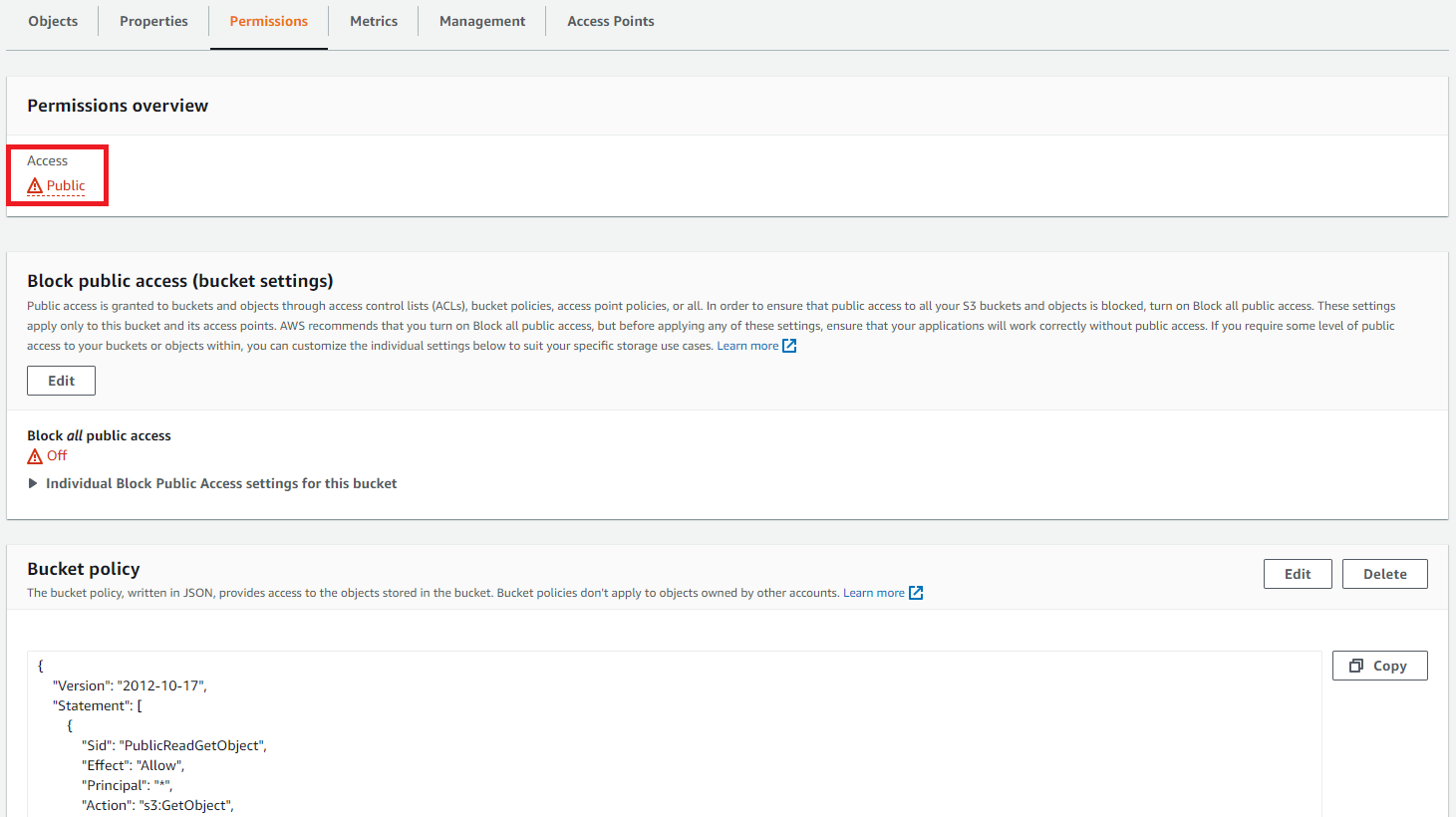
Connectors
update codes’ connection
Lambda function to Lambda function
| |
Lambda function to S3
Lambda function save/upload to S3
| |
Deploy
2 ways to manually CI/CD
Download and Upload
- Actions > Export function > Download deployment package

Export-function.png - (edit your code package)
- Compress your files > Upload from > .zip file

Upload-from-zip-file.png
Edit on the Portal
- Save
- Deploy